Until recently, organizations have had limited capabilities for assessing the damage that a cyberattack could do to their critical assets. Despite conducting penetration testing and red team testing, each of these approaches has limitations that prevent it from providing a comprehensive, dynamic and ongoing picture of an organization’s overall security posture.
Breach and Attack Simulation (BAS) solutions represent a new and emerging market and are directly adjacent to vulnerability assessment, according to The Market Guide for Vulnerability Assessment. They perform automated security testing: some challenge the existing security infrastructure and some model attack chains to identify the most-likely path an attacker would use to compromise an environment.
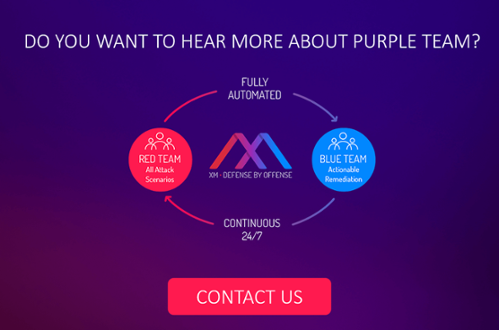
Purple Team: Simulate and Remediate
You may have heard of some other colors – like “yellow teaming” and “green teaming” – when referring to security, but security is not a crayon box. “Since these concepts did not have their origins in the military as do red and blue, I find them to be pointless buzzwords,” security specialist Haydn Johnson wrote in Tripwire.
A purple team is a well-known concept that blends the activities of both red team and blue team. The former is the security group that tests the organization against the attackers’ techniques and approaches used during real breaches. The latter is the company’s own IT/Security personnel who defend their organization’s around the clock. A purple team should enhance red and blue teams’ existing capabilities and allows them to exchange ideas, observations and insights more productively.
While traditional pen tests remain an invaluable tool for security testing and provide vital data for security evaluations, a purple team assessment is perfect for organizations with mature security postures that want to more thoroughly test how their security systems and processes work continuously in concert, explained security analyst Russel Van Tuyl at an article for Security Info Watch.
Always One Step Ahead of the Attacker
Despite implementing multiple solutions to create a defense in depth and following all industry best practices, organizations are still vulnerable to attacks. Hackers capitalize on human errors such as misconfigurations, shadow IT, and lack of awareness. They employ legitimate tools and user behavior to infiltrate networks and compromise assets. Also, you cannot always know if that new security solution that you’ve just bought is really your most urgent need. Do you really need it? Did you place it in the right place? With the right configuration?
A purple team assessment tests how well the pieces of the puzzle fit together and allows an organization to identify and remediate gaps. Our team has pulled together a few tips that will definitely help you secure your crown jewels – your critical assets and make you stay one step ahead of the attacker. Always.
- Always know the attack paths
Continuously identify attack vectors to your target assets 24×7. Prioritize actionable remediation.
- Reduce your IT hygiene risk
Deliver the big lift in IT hygiene. Address the whole spectrum of leveraging real user behavior to exploits.
- Optimize your cyber resources
Generate prioritized actionable remediation to improve the cybersecurity posture. Get insights into your security investments.
- Make data-driven decisions
Evaluate and implement best practices and policies with clear facts. Get your data at hand through reports and dashboards.
- Verify your security patches and fixes
Simulate your security mitigations and remediations before spending any time and money on implementing those fixes. Test the impact of those fixes repeatedly and automatically. Mitigating security risks can be hard, expensive and time-consuming, so simulating the remediation gives excellent insights before implementing any mitigation.
Harness the Power of Automated Purple Team
With an automated purple team running continuously, organizations are finally able to follow prioritized remediation guidelines and know as soon as an issue has been resolved. The move to automation empowers organizations with the ability to gain a worm’s eye view into new back doors and blind spots as soon as they appear and move to remediate them immediately without delay.
XM Cyber’s HaXM is the first fully automated Advanced Persistent Threat (APT) simulation and remediation platform to continuously expose attack vectors, from breach point to any organizational critical asset. This continuous loop of automated red teaming is completed by ongoing and prioritized actionable remediation of security gaps.
In effect, the solution operates as an automated purple team that fluidly combines red team and blue team processes to ensure that organizations are always one step ahead of the hacker. Addressing real user behavior, poor IT hygiene and security exploits, HaXM continuously leverages advanced offensive methods to expose the most critical blind spots.
Related Topics